comptia pt0-002 practice test
CompTIA PenTest+ Certification Exam
Last exam update: Jul 20 ,2024
Question 1
A company has hired a penetration tester to deploy and set up a rogue access point on the network. Which of the following is the BEST tool to use to accomplish this goal?
- A. Wireshark
- B. Aircrack-ng
- C. Kismet
- D. Wifite
Answer:
b
Question 2
An executive needs to use Wi-Fi to connect to the company's server while traveling. Looking for available Wi-Fi connections, the executive notices an available access point to a hotel chain that is not available where the executive is staying. Which of the following attacks is the executive MOST likely experiencing?
- A. Data modification
- B. Amplification
- C. Captive portal
- D. Evil twin
Answer:
d
Question 3
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0)
Gecko/20100101 Firefox/31.0
Accept-Language: en-US,en;q=0.5
Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
Network management interfaces are available on the production network.
An Nmap scan retuned the following:
Port State Service Version
22/tcp open ssh Cisco SSH 1.25 (protocol 2.0
80/tcp open http Cisco IOS http config
|_https-title: Did not follow redirect to https://10.50.100.16
443/tcp open https Cisco IOS https config
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
- A. Enforce enhanced password complexity requirements.
- B. Disable or upgrade SSH daemon.
- C. Disable HTTP/301 redirect configuration.
- D. Create an out-of-band network for management.
- E. Implement a better method for authentication.
- F. Eliminate network management and control interfaces.
Answer:
ae
Question 4
Which of the following can be used to store alphanumeric data that can be fed into scripts or programs as input to penetration-testing tools?
- A. Dictionary
- B. Directory
- C. Symlink
- D. Catalog
- E. For-loop
Answer:
a
Question 5
The following PowerShell snippet was extracted from a log of an attacker machine: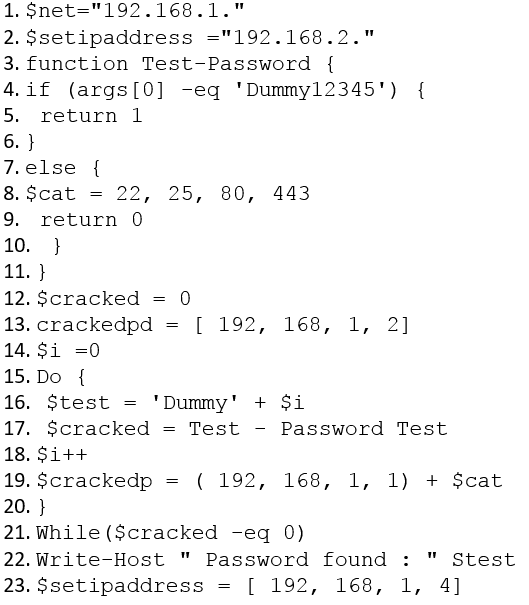
A penetration tester would like to identify the presence of an array. Which of the following line numbers would define the array?
- A. Line 8
- B. Line 13
- C. Line 19
- D. Line 20
Answer:
a
Question 6
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format: <name- serial_number>.
Which of the following would be the best action for the tester to take NEXT with this information?
- A. Create a custom password dictionary as preparation for password spray testing.
- B. Recommend using a password manager/vault instead of text files to store passwords securely.
- C. Recommend configuring password complexity rules in all the systems and applications.
- D. Document the unprotected file repository as a finding in the penetration-testing report.
Answer:
d
Question 7
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider's metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
- A. Cross-site request forgery
- B. Server-side request forgery
- C. Remote file inclusion
- D. Local code inclusion
Answer:
b
Question 8
A penetration tester exploited a vulnerability on a server and remotely ran a payload to gain a shell. However, a connection was not established, and no errors were shown on the payload execution. The penetration tester suspected that a network device, like an IPS or next-generation firewall, was dropping the connection. Which of the following payloads are MOST likely to establish a shell successfully?
- A. windows/x64/meterpreter/reverse_tcp
- B. windows/x64/meterpreter/reverse_http
- C. windows/x64/shell_reverse_tcp
- D. windows/x64/powershell_reverse_tcp
- E. windows/x64/meterpreter/reverse_https
Answer:
d
Question 9
A security analyst needs to perform an on-path attack on BLE smart devices. Which of the following tools would be BEST suited to accomplish this task?
- A. Wireshark
- B. Gattacker
- C. tcpdump
- D. Netcat
Answer:
b
Question 10
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees' phone numbers on the company's website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees' numbers?
- A. Web archive
- B. GitHub
- C. File metadata
- D. Underground forums
Answer:
a