Question 1
A user needs to read documentation on a device while walking around outdoors in bright sunlight.
Which of the following is the best type of device for this purpose?
- A. Laptop
- B. Tablet
- C. E-reader
- D. ISmartphone
Answer:
C
Explanation:
E-readers use e-ink displays, which are highly readable in bright sunlight and have long battery life —
ideal for outdoor use.
Laptops, tablets, and smartphones often have glare or brightness issues in direct sunlight.
Comments
Question 2
A user attempts to log in to a website and receives a prompt to update their password. Which of the
following is this an example of?
- A. Password privacy
- B. Password history
- C. Password complexity
- D. Password expiration
Answer:
D
Explanation:
A prompt to update a password during login typically indicates that the password has expired based
on the system's policy.
Other options:
● Password history prevents reuse of old passwords,
● Password complexity sets rules for character requirements,
● Password privacy involves keeping the password confidential.
Comments
Question 3
Which of the following types of AI is used to edit images?
- A. Assistive
- B. Predictive
- C. Chatbot
- D. Generative
Answer:
D
Explanation:
Generative AI creates or modifies content, such as editing images, generating art, or producing
media.
Other options:
● Assistive AI supports tasks,
● Predictive AI forecasts outcomes,
● Chatbots simulate conversation but do not edit images.
Comments
Question 4
Given the following pseudocode:
<BODY>
<P>This is a paragraph.</P>
</BODY>
Which of the following best represents the type of language used by this code?
- A. Markup
- B. Query
- C. Compiled
- D. Scripting
Answer:
A
Explanation:
The code shown uses HTML tags like <BODY> and <P>, which are part of a markup language. Markup
languages describe the structure and presentation of text, not logic or computation.
Other options:
● Query languages retrieve data (e.g., SQL),
● Compiled languages are turned into machine code (e.g., C++),
● Scripting languages execute instructions (e.g., Python, JavaScript).
Comments
Question 5
Which of the following can be used to input commands for a computer to execute?
- A. Services
- B. Attributes
- C. Process
- D. Console
Answer:
D
Explanation:
A console (or command-line interface) allows users to input commands for the computer to execute
directly.
Other options:
● Services run background tasks,
● Attributes describe properties of objects,
● Process refers to a running program, not a command input method.
Comments
Question 6
Which of the following is the last tool that should be used when creating a custom-length network
cable?
- A. Cable tester
- B. Crimper
- C. Wire cutter
- D. Ethernet connector
Answer:
A
Explanation:
The cable tester is used last to verify the cable functions correctly after cutting, attaching connectors
with a crimper, and assembling the Ethernet cable.
Wire cutter, Ethernet connector, and crimper are used earlier in the cable creation process.
Comments
Question 7
Given the following pseudocode:
10 FOR Q=1 TO 100
20 PRINT Q
30 NEXT Q
40 EXIT
Which of the following best represents line 10?
- A. Attribute
- B. Sequence
- C. Branch
- D. Loop
Answer:
D
Explanation:
Line 10 (FOR Q=1 TO 100) initializes a loop that iterates from 1 to 100.
Other options:
● Sequence refers to a straight execution of instructions,
● Branch involves decision-making (e.g., IF...THEN),
● Attribute is a descriptive property, not a control structure.
Comments
Question 8
A user is logged in but unable to access a shared folder on the network. Which of the following
security concepts is in place?
- A. Authentication
- B. Authorization
- C. Accounting
- D. Non-repudiation
Answer:
B
Explanation:
Authorization determines what a user is allowed to access after they have logged in. The user is
already authenticated (logged in), but lacks permission to access the shared folder, indicating an
authorization issue.
Other options:
● Authentication verifies identity,
● Accounting tracks user actions,
● Non-repudiation ensures actions cannot be denied later.
Comments
Question 9
Given the following table: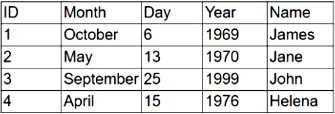
Which of the following fields best represents a primary key?
- A. ID
- B. Month
- C. Day
- D. Year
- E. Name
Answer:
A
Explanation:
The ID field contains unique values for each record and is typically used as a primary key in a
database. A primary key uniquely identifies each row in a table.
Month, Day, Year, and Name may have duplicates and do not guarantee uniqueness.
Comments
Question 10
A technician needs to install input devices while setting up a new desktop PC. Which of the following
should the technician install? (Choose two.)
- A. Printer
- B. Mouse
- C. Keyboard
- D. CPU
- E. Speaker
- F. SSD
Answer:
B, C
Explanation:
A mouse and keyboard are standard input devices used to interact with a desktop PC.
Other options:
● Printer and speaker are output devices,
● CPU is a processing unit,
● SSD is a storage device.
Comments
Page 1 out of 10
Viewing questions 1-10 out of 108
page 2