Question 1
Refer to the exhibit.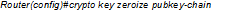
Which effect of this command is true?
- A. The route immediately deletes its current public key from the cache and generates a new one.
- B. The public key of the remote peer is deleted from the router cache.
- C. The CA revokes the public key certificate of the router.
- D. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.
- E. The router sends a request to the CA to delete the router certificate from its configuration.
Answer:
B
Comments
Question 2
Which two statements about a wireless access point configured with the guest-mode command are
true?
(Choose two.)
- A. It can support more than one guest-mode SSID.
- B. It supports associations by clients that perform passive scans.
- C. It allows clients configured without SSIDs to associate.
- D. It allows associated clients to transmit packets using its SSID.
- E. If one device on a network is configure in guest-mode, clients can use the guest-mode SSID to connect to any device in the same network.
Answer:
BC
Comments
Question 3
Refer to the exhibit.
Which two statements about a device with this configuration are true? (Choose two.)
- A. When a peer establishes a new connection to the device, CTS retains all existing SGT mapping entries for 3 minutes.
- B. If a peer reconnects to device within 120 seconds of terminating a CTS-SXP connection, the reconciliation timer stats.
- C. When a peer re-establishes a previous connection to the device, CTS retains all existing SGT mapping entries for 3 minutes.
- D. If a peer reconnects to device within 180 seconds of terminating a CTS-SXP connection, the reconciliation timer stats.
- E. If a peer re-establishes a connection to the device before the hold-down timer expires, the device retains the SGT mapping entries it learned during the previous connection for an additional 3 minutes.
- F. It sets the internal hold-down timer of the device to 3 minutes.
Answer:
BE
Comments
Question 4
Which option is a data modeling language used to model configuration and state data of network
elements?
- A. RESTCONF
- B. SNMPv4
- C. NETCONF
- D. YANG
Answer:
D
Comments
Question 5
Which statement about MDM with the Cisco ISE is true?
- A. The MDM’s server certificate must be imported into the Cisco ISE Certificate Store before the MDM and ISE can establish a connection.
- B. MDM servers can generate custom ACLs for the Cisco ISE to apply to network devices.
- C. The Cisco ISE supports a built-in list of MDM dictionary attributes it can use in authorization policies.
- D. The Cisco ISE supports limited built-in MDM functionality.
- E. If a mobile endpoint fails posture compliance, both the user and the administrator are notified immediately.
- F. When a mobile endpoint becomes compliant the Cisco ISE records the updated device status in its internal database.
Answer:
A
Explanation:
Mobile Device Management
https://meraki.cisco.com/blog/tag/mobile-device-management/
Comments
Question 6
Refer to the exhibit.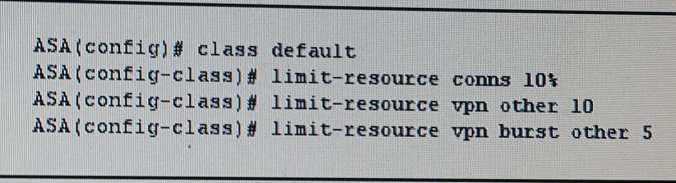
What is the maximum number of site-to-site VPNs allowed by this configuration?
- A. 10
- B. unlimited
- C. 5
- D. 0
- E. 1
- F. 15
Answer:
F
Comments
Question 7
When applying MD5 route authentication on routers running RIP or EIGRP, which two important key
chain considerations should be accounted for? (Choose two.)
- A. Key 0 of all key chains must match for all routers in the autonomous system.
- B. The lifetimes of the keys in the chain should overlap.
- C. Routers should be configured for NTP to synchronize their clocks.
- D. No more than three keys should be configured in any single chain.
- E. Link compression techniques should be disabled on links transporting any MD5 hash.
Answer:
BC
Comments
Question 8
Which description of SaaS is true?
- A. a service offering on-demand licensed applications for end users
- B. a service offering that allowing developers to build their own applications
- C. a service offering on-demand software downloads
- D. a service offering a software environment in which applications can be build and deployed.
Answer:
A
Comments
Question 9
Which two statements about ICMP redirect messages are true? (Choose two.)
- A. Redirects are only punted to the CPU if the packets are also source-routed.
- B. The messages contain an ICMP Type 3 and ICMP code 7.
- C. By default, configuring HSRP on the interface disables ICMP redirect functionality.
- D. They are generated when a packet enters and exits the same route interface.
- E. They are generated by the host to inform the router of an temate route to the destination.
Answer:
CD
Comments
Question 10
Refer to the exhibit.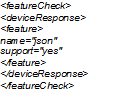
Which data format is used in this script?
- A. JSON
- B. YANG
- C. API
- D. XML
- E. JavaScript
Answer:
D
Comments
Page 1 out of 51
Viewing questions 1-10 out of 514
page 2