Question 1
In the zero-trust network access model, which criteria is used for continuous verification to modify
trust levels?
- A. System patching status
- B. Detected threat levels
- C. User and device behavior
- D. Network traffic patterns
Answer:
C
Comments
Question 2
Refer to the exhibit.
Refer to the exhibit. An engineer must create a segmentation policy in Cisco Secure Workload to
block HTTP traffic. The indicated configuration was applied; however, HTTP traffic is still allowed.
What should be done to meet the requirement?
- A. Change consumer_filter_ref to HTTP Consumer.
- B. Add HTTP to 14_params.
- C. Decrease the priority of the template to 50.
- D. Increase the priority of the template to 200.
Answer:
B
Comments
Question 3
Refer to the exhibit.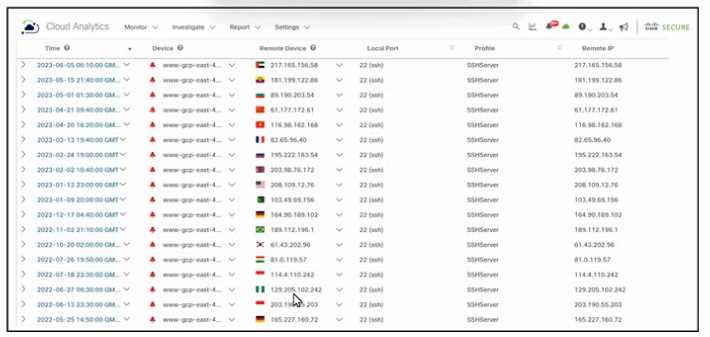
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is
occurring?
- A. Persistent remote-control connections
- B. Distributed DDoS attack
- C. Geographically unusual remote access
- D. Memory exhaustion attempt toward port 22
Answer:
C
Comments
Question 4
Refer to the exhibit.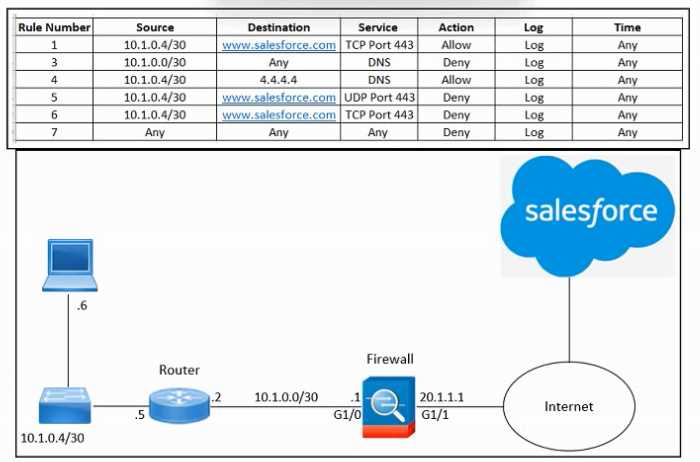
Refer to the exhibit. An engineer must configure the Cisco ASA firewall to allow the client with IP
address 10.1.0.6 to access the Salesforce login page at https://www.salesforce.com. The indicated
configuration was applied to the firewall and public DNS 4.4.4.4 is used for name resolution;
however, the client still cannot access the URL. What should be done to meet the requirements?
- A. Remove rule 3
- B. Move rule 5 to the top
- C. Remove rule 7
- D. Move rule 6 to the top
Answer:
A
Comments
Question 5
Refer to the exhibit.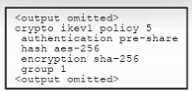
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use
AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall;
however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the
requirement? (Choose two.)
- A. encryption aes-256
- B. ipsec-proposal sha-256-aes-256
- C. integrity aes-256
- D. ipsec-proposal AES256-SHA256
- E. hash sha-256
Answer:
A, E
Comments
Question 6
Which method is used by a Cisco XDR solution to prioritize actions?
- A. Updating antivirus signatures
- B. Monitoring endpoint activity
- C. Leveraging AI and machine learning
- D. Analyzing network traffic patterns
Answer:
C
Comments
Question 7
DRAG DROP
Drag and drop the five core functions from the left into the order defined by the NIST Cyber security
Framework on the right.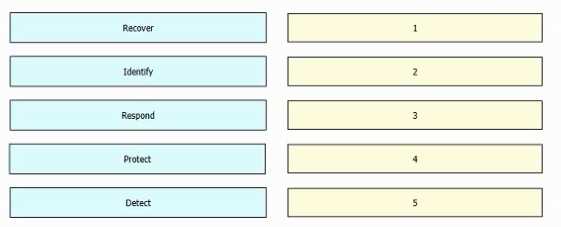
Answer:
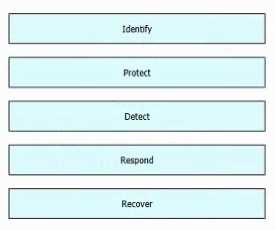
Comments
Question 8
Refer to the exhibit.
Refer to the exhibit. An engineer must configure a global allow list in Cisco Umbrella for the
cisco.com domain. All other domains must be blocked. After creating a new policy and adding the
cisco.com domain, the engineer attempts to access a site outside of cisco.com and is successful.
Which additional Security Settings action must be taken to meet the requirement?
- A. Limit Content Access.
- B. Enforce SafeSearch.
- C. Enable Allow-Only Mode
- D. Apply Destination List.
Answer:
C
Comments
Question 9
An administrator received an incident report indicating suspicious activity of a user using a corporate
device. The manager requested that the credentials of user [email protected] be reset and synced via
the Active Directory. Removing the account should be avoided and used for further investigation on
data leak. Which configuration must the administrator apply on the Duo Admin Panel?
- A. Delete the user in the Users tab option and sync it with the domain controller.
- B. Quarantine the user from all the policies on the Policies tab, including associated devices.
- C. Request the password change on the Device tab on managed devices.
- D. Disable the account on the Users tab and reset the password from the Active Directory.
Answer:
D
Comments
Question 10
What helps prevent drive-by compromise?
- A. Ad blockers
- B. VPN
- C. Incognito browsing
- D. Browsing known websites
Answer:
A
Comments
Page 1 out of 6
Viewing questions 1-10 out of 61
page 2