cisco 300-725 practice test
Securing the Web with Cisco Web Security Appliance (SWSA)
Last exam update: Jul 20 ,2024
Question 1
When an access policy is created, what is the default option for the Application Settings?
- A. Use Global Policy Applications Settings
- B. Define the Applications Custom Setting
- C. Set all applications to Block
- D. Set all applications to Monitor
Answer:
B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01111.html
Question 2
Which type of FTP proxy does the Cisco WSA support?
- A. non-native FTP
- B. FTP over UDP tunneling
- C. FTP over HTTP
- D. hybrid FTP
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117984-qanda-wsa-00.html
Question 3
Which two types of reports are scheduled on the Cisco WSA to analyze traffic? (Choose two.)
- A. Layer 3 traffic monitor
- B. URL categories
- C. host statistics
- D. application visibility
- E. system capacity
Answer:
A D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_010101.pdf (8)
Question 4
Which port is configured in a browser to use the Cisco WSA web proxy with default settings?
- A. 8080
- B. 8443
- C. 8021
- D. 3128
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/Aug2013/CVD-
WebSecurityUsingCiscoWSADesignGuide-AUG13.pdf (16)
Question 5
What is needed to enable an HTTPS proxy?
- A. self-signed server certificate
- B. trusted third-party CA signed root certificate
- C. self-signed CSR
- D. self-signed root certificate
Answer:
C
Explanation:
Reference: https://community.cisco.com/t5/web-security/cisco-wsa-https-proxy-certificate-issue/td-p/3019392
Question 6
Which method is used by AMP against zero-day and targeted file-based attacks?
- A. analyzing behavior of all files that are not yet known to the reputation service
- B. periodically evaluating emerging threats as new information becomes available
- C. implementing security group tags
- D. obtaining the reputation of known files
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/solution-
overview-c22-734228.html
Question 7
Which action is a valid default for the Global Access Policy in the Application Visibility Control engine on the Cisco WSA?
- A. bandwidth limit
- B. permit
- C. restrict
- D. monitor
Answer:
D
Explanation:
Reference: https://hrouhani.org/cisco-web-security-appliance-ironport/
Question 8
Which two configuration options are available on a Cisco WSA within a decryption policy? (Choose two.)
- A. Pass Through
- B. Warn
- C. Decrypt
- D. Allow
- E. Block
Answer:
A C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01011.html
Question 9
Which configuration mode does the Cisco WSA use to create an Active Directory realm for Kerberos authentication?
- A. Forward
- B. Connector
- C. Transparent
- D. Standard
Answer:
D
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_01001.html#con_1406137
Question 10
Which statement about configuring an identification profile for machine authentication is true?
- A. Cloud Web Security Connector mode with an active directory enabled supports machine authentication
- B. Identification profile machine ID is supported locally, but the Cisco WSA does not support machine ID authentication
- C. Cloud Web Security with Kerberos enabled supports machine authentication
- D. If an Active Directory realm is used, identification can be performed for an authenticated user or IP address but not for a machine ID
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_01001.html
Question 11
A user browses to a company website that is categorized as Business and Industry and contains a Facebook post. The
user cannot see the Facebook post because the category Social Networking is blocked.
Which configuration allows the user to see the Facebook post?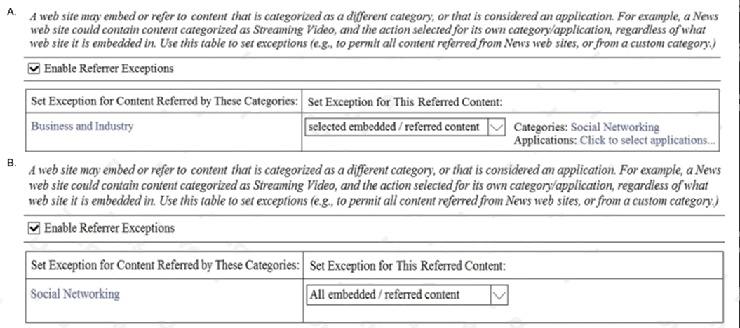
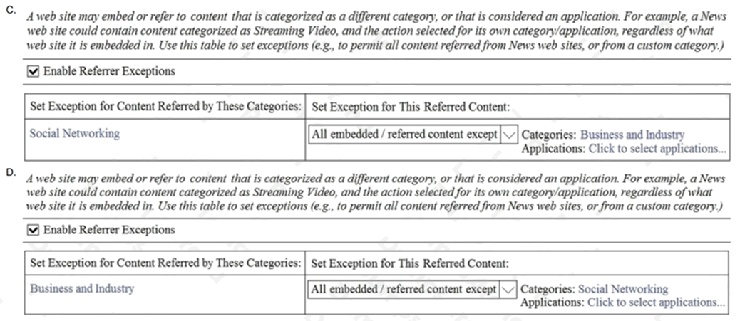
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
A
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01001.html
Question 12
What must be configured first when creating an access policy that matches the Active Directory group?
- A. authentication, authorization, and accounting of groups
- B. FQDN specification
- C. authentication realm
- D. authorized groups specification
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/118005-configure-ntlm-00.html
Question 13
Which response code in the access logs indicates that a transaction was blocked due to policy?
- A. TCP_DENIED/407
- B. TCP_DENIED/401
- C. TCP_DENIED/403
- D. TCP_DENIED/307
Answer:
A
Explanation:
Reference: https://docuri.com/download/instructions_59a8d562f581719e12ad43fe_pdf
Question 14
What must be configured to require users to click through an acceptance page before they are allowed to go to the Internet
through the Cisco WSA?
- A. Enable End-User Acknowledgement Page and set to Required in Identification Profiles
- B. Enable End -User URL Filtering Warning Page and set to Required in Identification Profiles
- C. Enable End-User Acknowledgement Page and set to Required in Access Policies
- D. Enable End-User URL Filtering Warning Page and set to Required in Access Policies
Answer:
C
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_010100.html
Question 15
How does the Cisco WSA choose which scanning engine verdict to use when there is more than one verdict?
- A. based on the least restrictive verdict
- B. based on the most restrictive verdict
- C. based on the first verdict returned
- D. based on the last verdict returned
Answer:
B
Explanation:
Reference: https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-
0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_010000.html