Question 1
Refer to the exhibit: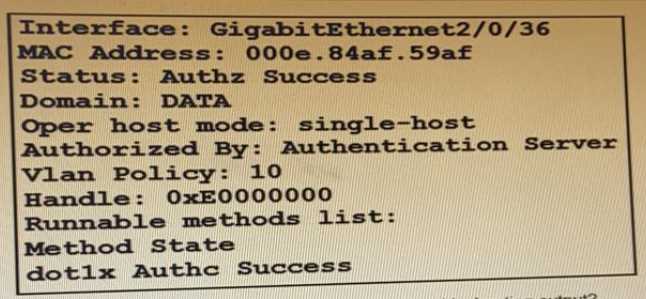
Which command is typed within the CU of a switch to view the troubleshooting output?
- A. show authentication sessions mac 000e.84af.59af details
- B. show authentication registrations
- C. show authentication interface gigabitethemet2/0/36
- D. show authentication sessions method
Answer:
A
Comments
Question 2
What must be configured on the Cisco ISE authentication policy for unknown MAC
addresses/identities for successful authentication?
- A. pass
- B. reject
- C. drop
- D. continue
Answer:
D
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_id_stores.html
Comments
Question 3
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so
that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
- A. NetFlow
- B. SNMP
- C. HTTP
- D. DHCP
- E. RADIUS
Answer:
D, E
Explanation:
Cisco ISE implements an ARP cache in the profiling service, so that you can reliably map the IP
addresses and the MAC addresses of endpoints. For the ARP cache to function, you must enable
either the DHCP probe or the RADIUS probe. The DHCP and RADIUS probes carry the IP addresses
and the MAC addresses of endpoints in the payload data. The dhcp-requested address attribute in
the DHCP probe and the Framed-IP-address attribute in the RADIUS probe carry the IP addresses of
endpoints, along with their MAC addresses, which can be mapped and stored in the ARP cache.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010100.html
Comments
Question 4
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from
the Cisco ISE node?
- A. session timeout
- B. idle timeout
- C. radius-server timeout
- D. termination-action
Answer:
B
Explanation:
When the inactivity timer is enabled, the switch monitors the activity from authenticated endpoints.
When the inactivity timer expires, the switch removes the authenticated session. The inactivity timer
for MAB can be statically configured on the switch port, or it can be dynamically assigned using the
RADIUS Idle-Timeout attribute
Comments
Question 5
What must match between Cisco ISE and the network access device to successfully authenticate
endpoints?
- A. SNMP version
- B. shared secret
- C. certificate
- D. profile
Answer:
B
Explanation:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_network_devices.html
Comments
Question 6
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal?
(Choose two )
- A. Random
- B. Monthly
- C. Daily
- D. Imported
- E. Known
Answer:
A, D
Comments
Question 7
How is policy services node redundancy achieved in a deployment?
- A. by enabling VIP
- B. by utilizing RADIUS server list on the NAD
- C. by creating a node group
- D. by deploying both primary and secondary node
Answer:
C
Comments
Question 8
If a user reports a device lost or stolen, which portal should be used to prevent the device from
accessing the network while still providing information about why the device is blocked?
- A. Client Provisioning
- B. Guest
- C. BYOD
- D. Blacklist
Answer:
D
Explanation:
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Borderless_Networks/Unified_Access/BYOD_Design_Guide/Managing_Lost_or_Stolen_Device.html#90273
The Blacklist identity group is system generated and maintained by ISE to prevent access to lost or
stolen devices. In this design guide, two authorization profiles are used to enforce the permissions
for wireless and wired devices within the Blacklist:
Blackhole WiFi Access
Blackhole Wired Access
Comments
Question 9
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server.
Which command is the user missing in the switch’s configuration?
- A. radius-server vsa send accounting
- B. aaa accounting network default start-stop group radius
- C. aaa accounting resource default start-stop group radius
- D. aaa accounting exec default start-stop group radios
Answer:
A
Comments
Question 10
What are two benefits of TACACS+ versus RADIUS for device administration? (Choose two )
- A. TACACS+ supports 802.1X, and RADIUS supports MAB
- B. TACACS+ uses UDP, and RADIUS uses TCP
- C. TACACS+ has command authorization, and RADIUS does not.
- D. TACACS+ provides the service type, and RADIUS does not
- E. TACACS+ encrypts the whole payload, and RADIUS encrypts only the password.
Answer:
C, E
Comments
Page 1 out of 30
Viewing questions 1-10 out of 306
page 2