Question 1
When should the API Inspector be used?
- A. to send an API request to the APIC
- B. to learn or identify the sequence of API calls for a specific operation in the APIC GUI
- C. to verify the XML structure of an object based on a specific operation in the APIC GUI
- D. to launch an Ansible playbook
Answer:
B
Reference: Devnet training
Comments
Question 2
A set of automation scripts work with no issue from a local machine, but an experiment needs to
take place with a new package found online.
How is this new package isolated from the main code base?
- A. Add the new package to your requirements txt file.
- B. Create a new virtual machine and perform a pip install of the new package
- C. Perform a pip install of the new package when logged into your local machine as root
- D. Create a new virtual environment and perform a pip install of the new package
Answer:
D
Reference: Devnet Training
Comments
Question 3
DRAG DROP
When a switch boots it does not find its startup-config file. Drag and drop the steps that Power-On
Auto Provisioning goes through to configure the switch for remote management from the left into
the correct order on the right. Not all options are used.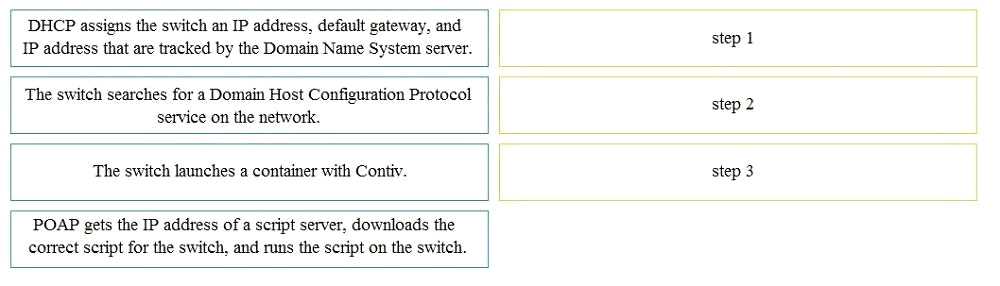
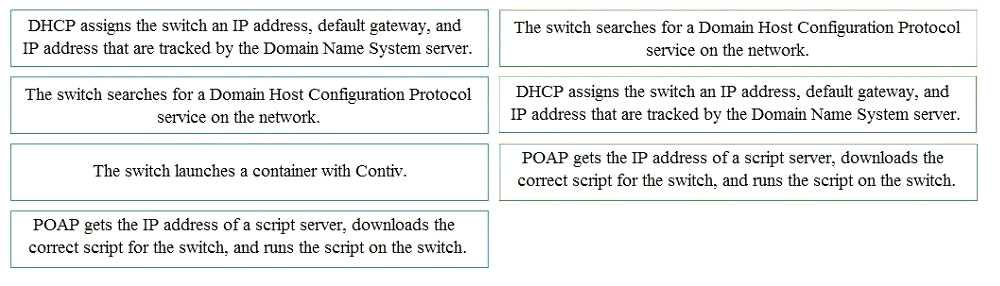
Answer
Step 1 : The switch searches for a Domain Host Configuration Protocol service on the network
Step 2 : DHCP assigns the switch an IP Address, default gateway, and IP address that are tracked by
the Domain Name System server.
Step 3 : POAP gets the IP address of a script server, downloads the correct script for the switch, and
runs the script on the switch.
Answer:
D
Comments
Question 4
Which Cisco UCS PowerTool commands initiate a Cisco UCS Manager connection?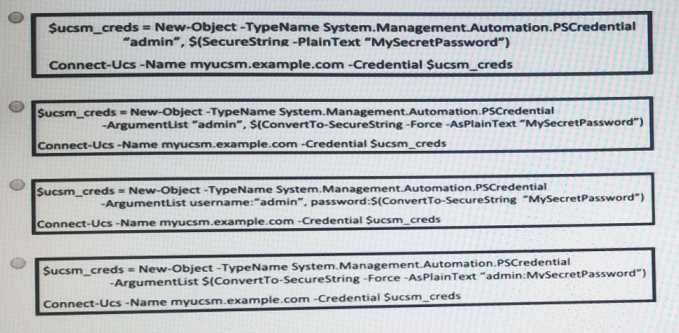
- D. Option
Answer:
B
Reference:
https://blogs.cisco.com/developer/cisco-ucs-automation-part2-a-step-by-step-guide-to-
connecting-and-disconnecting-using-ucs-powertool
Comments
Question 5
What are two differences between SNMP and model-driven telemetry? (Choose two.)
- A. SNMP uses a continuous stream model
- B. SNMP uses a push model O SNMP uses a pull model
- C. Model-driven telemetry uses a pull model
- D. Model-driven telemetry uses a push model
Answer:
BD
Reference:
https://blogs.cisco.com/developer/its-time-to-move-away-from-snmp-and-cli-and-use-
model-driven-
telemetry#:~:text=SNMP%20uses%20the%20pull%20model%20when%20retrieving%20data%20fro
m%20a%20switch.&text=SNMP%20also%20uses%20push%20model,limits%20like%20scale%20and
%20efficiency.
Comments
Question 6
Which two bootstrap technologies are supported by Cisco NX-OS platforms? (Choose two )
- A. iPXE
- B. PNP
- C. POAP
- D. BOOTP
- E. DHCP
Answer:
CE
Comments
Question 7
Refer to the exhibit: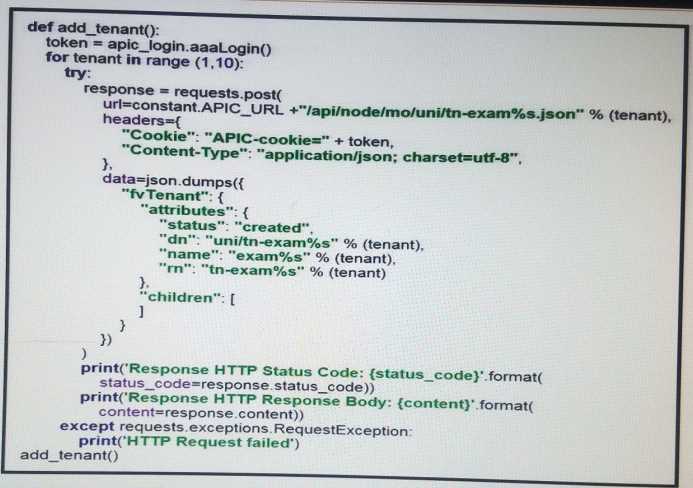
Assuming a new ACI instance what is the result when this script is run?
- A. Ten objects are created and subsequently deleted
- B. Nine objects are created
- C. An exception is thrown
- D. Ten objects are created
Answer:
B
Comments
Question 8
Which Ansible playbook creates a new VLAN 10 named Web?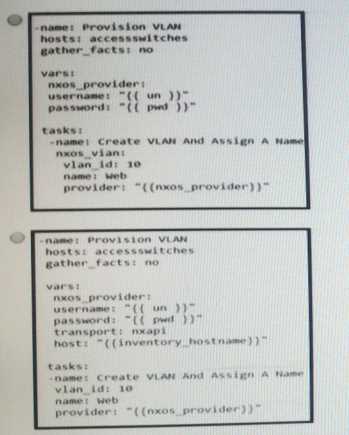

- D. Option
Answer:
D
Reference:
https://docs.ansible.com/ansible/latest/modules/nxos_vlan_module.html
Comments
Question 9
Which two statements about gRPC are true? (Choose two )
- A. It is an IETF draft
- B. It is an IETF standard
- C. It runs over SSH
- D. It is an open source initiative
- E. It runs over HTTPS
Answer:
AD
Comments
Question 10
Which Ansible playbook fragment returns the fewest queried ACI endpoint groups?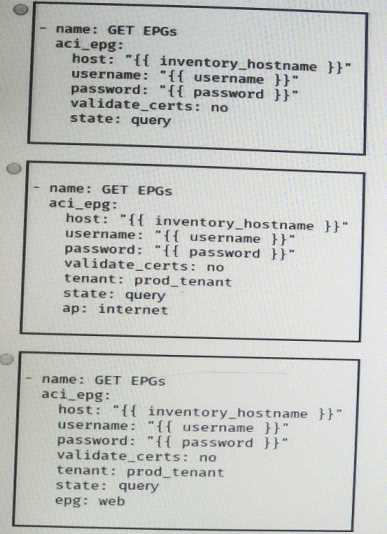
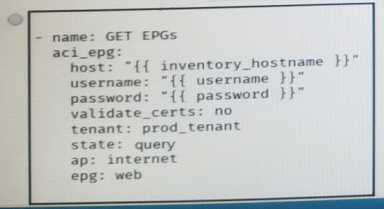
- D. Option
Answer:
D
Reference:
https://docs.ansible.com/ansible/latest/modules/aci_epg_module.html
Comments
Page 1 out of 7
Viewing questions 1-10 out of 75
page 2