Question 1
Refer to the exhibit.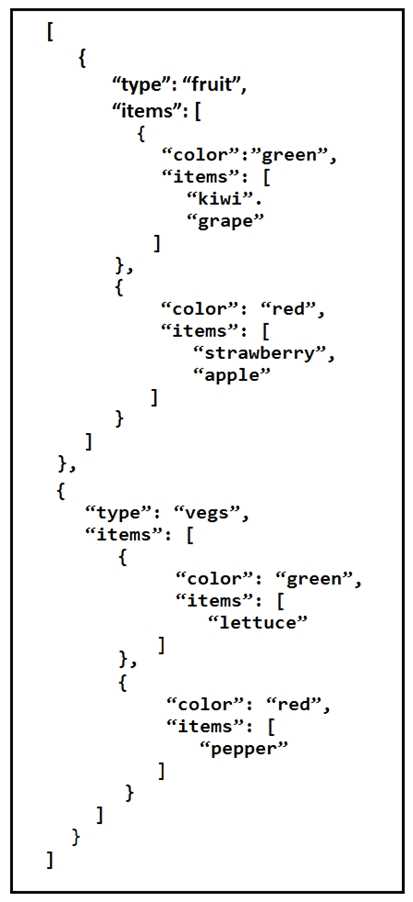
A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called
“vegetables” Using python, which output is the result of this command?
- A. Lettuce
- B. Kiwi
- C. [‘kiwi’, ‘grape’]
- D. {‘color’: ‘green’, ‘items’: [‘kiwi’, ‘grape’]
Answer:
B
Explanation:
Understand the JSON Structure: The JSON data given in the exhibit consists of an array of objects.
Each object has a type and an items key. The items key contains an array of objects, each with a color
and another items key, which is an array of strings representing items of that color.
Analyze the Python Code: The Python code provided is:
print(filter(lambda l: l['type'] == 'fruit', vegetables)[0]['items'][0]['items'][0])
Break Down the Code:
filter(lambda l: l['type'] == 'fruit', vegetables): This line filters the JSON array vegetables to include
only objects where the type is 'fruit'.
filter(...)[0]: After filtering, this selects the first object in the filtered list, which is the fruit object.
['items'][0]: This accesses the first item in the items array of the fruit object. In this case, it refers to
the object where color is "green".
['items'][0]: This accesses the first item in the items array of the green object, which is "kiwi".
Evaluate the Code:
The first object of type fruit in the JSON is found.
The first item in the items array for fruit with the color green is selected.
The first item in this nested items array is "kiwi".
Therefore, the output of the given Python command is "Kiwi".
Reference:
Python documentation on filter:
Python Docs - Filter
JSON structure understanding from DevNet Associate study materials on API interactions and data
parsing.
Comments
Question 2
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
- A. 400
- B. 403
- C. 405
- D. 429
Answer:
A
Explanation:
The HTTP status code 400 (Bad Request) is used by a REST API to indicate that the server cannot or
will not process the request due to something that is perceived to be a client error (e.g., malformed
request syntax, invalid request message framing, or deceptive request routing).
Reference:
Cisco DevNet Associate Certification Guide: Chapter on RESTful APIs and HTTP methods, specifically
on status codes.
HTTP/1.1 documentation: Status Code Definitions from the W3C.
Comments
Question 3
What is the purpose of a MAC address?
- A. To uniquely identify a router in a LAN
- B. To uniquely identify a network interface in a LAN
- C. To uniquely identify a device on the internet
- D. To uniquely identify a switch in a LAN
Answer:
B
Explanation:
A MAC (Media Access Control) address is a unique identifier assigned to a network interface card
(NIC) for communications at the data link layer of a network segment. MAC addresses are used
within local area networks (LANs) to ensure that data packets are delivered to the correct hardware
device. Every network interface on a device, such as a computer, router, or switch, has a unique MAC
address.
Reference: Cisco - MAC Addresses
Comments
Question 4
Which way should be used to safely the API keys?
- A. In an environment variable unique to the system database
- B. Encrypted in a configuration file that is separate from the code
- C. Encrypted in the code in a function
- D. Plain text in the code as a constant
Answer:
B
Explanation:
API keys should be stored securely to prevent unauthorized access. The best practice is to store them
encrypted in a configuration file that is separate from the code. This approach ensures that sensitive
information is not hardcoded in the source code, which could be exposed through version control or
other means. Keeping API keys in encrypted configuration files also allows for better management
and updating of keys without changing the application code.
Reference: Cisco Secure Coding Practices
Comments
Question 5
Refer to the exhibit.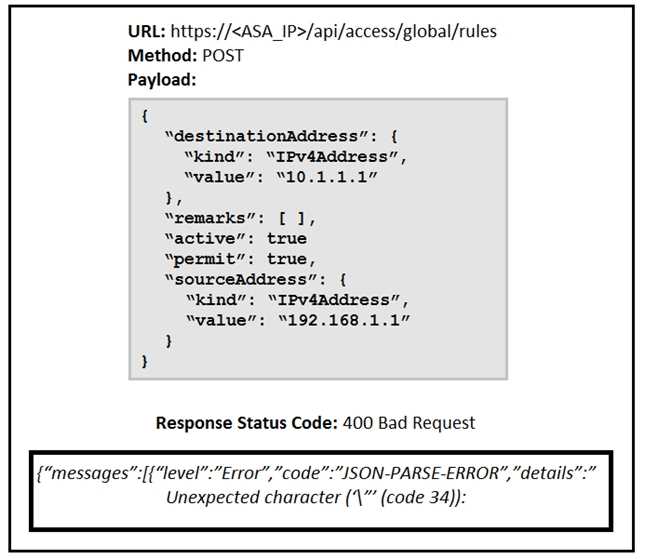
What caused the error in this API request?
- A. The API resource does not support the POST operation
- B. The API resource does not support JSON format payloads.
- C. The submitted JSON payload includes a field that is not supported by the API resource.
- D. The submitted JSON payload has a formatting issue
Answer:
D
Explanation:
The error message "JSON-PARSE-ERROR" and "Unexpected character ('"' (code 34))" indicates a
problem with the formatting of the JSON payload. Specifically, there are likely incorrect characters or
misplaced quotes within the JSON structure. JSON formatting issues are common errors that can
occur due to syntax mistakes such as missing commas, incorrect braces, or invalid characters.
To resolve this, carefully check the JSON structure for proper formatting, ensuring all fields are
correctly defined and that syntax rules are followed.
Reference: Cisco API Troubleshooting
Comments
Question 6
DRAG DROP
Drag and drop elements of the RESTCONF protocol stack from the left onto the correct description on
the right. Not all elements on the left are used.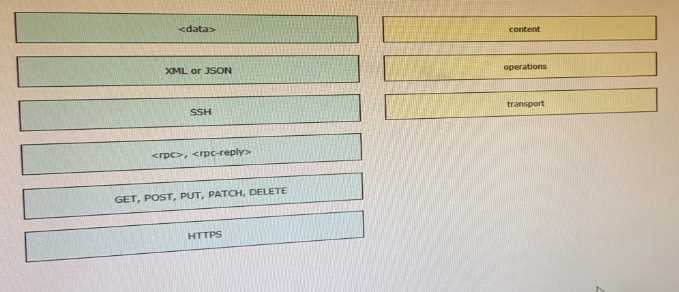
Answer:
None
Explanation: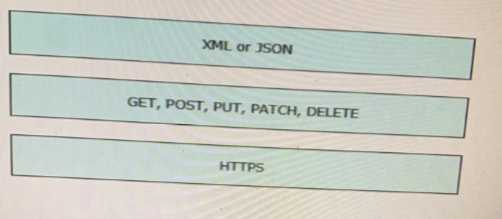
1 – B, 2 – E, 3 - F
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-
xml/ios/prog/configuration/169/b_169_programmability_cg/restconf_programmable_interface.htm
l
Comments
Question 7
What are two advantages of version control software? (Choose two.)
- A. It supports tracking and comparison of changes in binary formate files.
- B. It allows old versions of packaged applications to be hosted on the Internet
- C. It provides wiki collaboration software for documentation.
- D. It supports comparisons between revisions of source code files.
- E. It allows new team members to access the current code and history.
Answer:
DE
Explanation:
Version control software offers numerous benefits to development teams. Key advantages include:
Comparisons between revisions of source code files: Version control allows developers to compare
different versions of source code files, track changes, and identify what modifications were made and
by whom. This is essential for debugging and maintaining code quality.
Access to current code and history for new team members: New team members can quickly get up to
speed by accessing the current version of the code and the entire history of changes. This
transparency facilitates onboarding and improves collaboration among team members.
Reference: Cisco DevNet Version Control
Comments
Question 8
Which description of a default gateway if true?
- A. It is a device that receives IP packets that have no explicit next-hop in the routing table.
- B. It is a feature that translates between public and private addresses.
- C. It is a security feature that denies certain traffic.
- D. It is a device that receives Layer 2 frames with an unknown destination address.
Answer:
A
Explanation:
A default gateway serves as an access point or IP router that a networked computer uses to send
information to a computer in another network or the internet. It is essentially the forwarding node
that routes traffic from a local network to other networks. When an IP packet's destination is not
within the local network and no specific route is defined in the routing table, the packet is sent to the
default gateway.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on Networking Basics and Routing
Fundamentals.
Cisco Documentation on Default Gateway and Routing.
Comments
Question 9
DRAG DROP
Drag and drop the HTTP methods from the left onto their generally accepted corresponding create,
read, update, and delete operations on the right.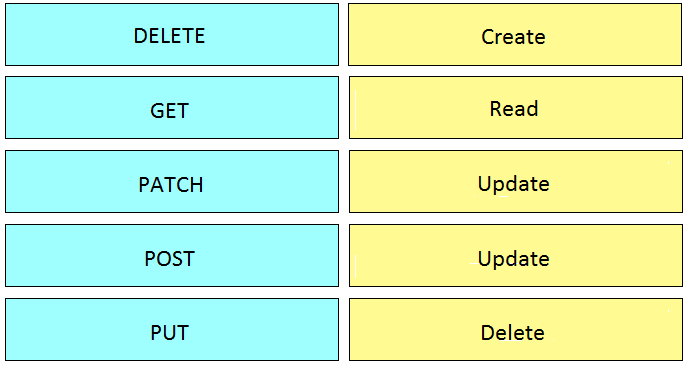
Answer:
None
Explanation:
1 – D, 2 – B, 3 – C, 4 – E, 5 – A
Reference:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/application-policy-
infrastructure-controller-enterprise-module/1-2-x/config-guide/b_apic-em_config_guide_v_1-2-
x/b_apic-em_config_guide_v_1-2-x_chapter_01001.pdf
OR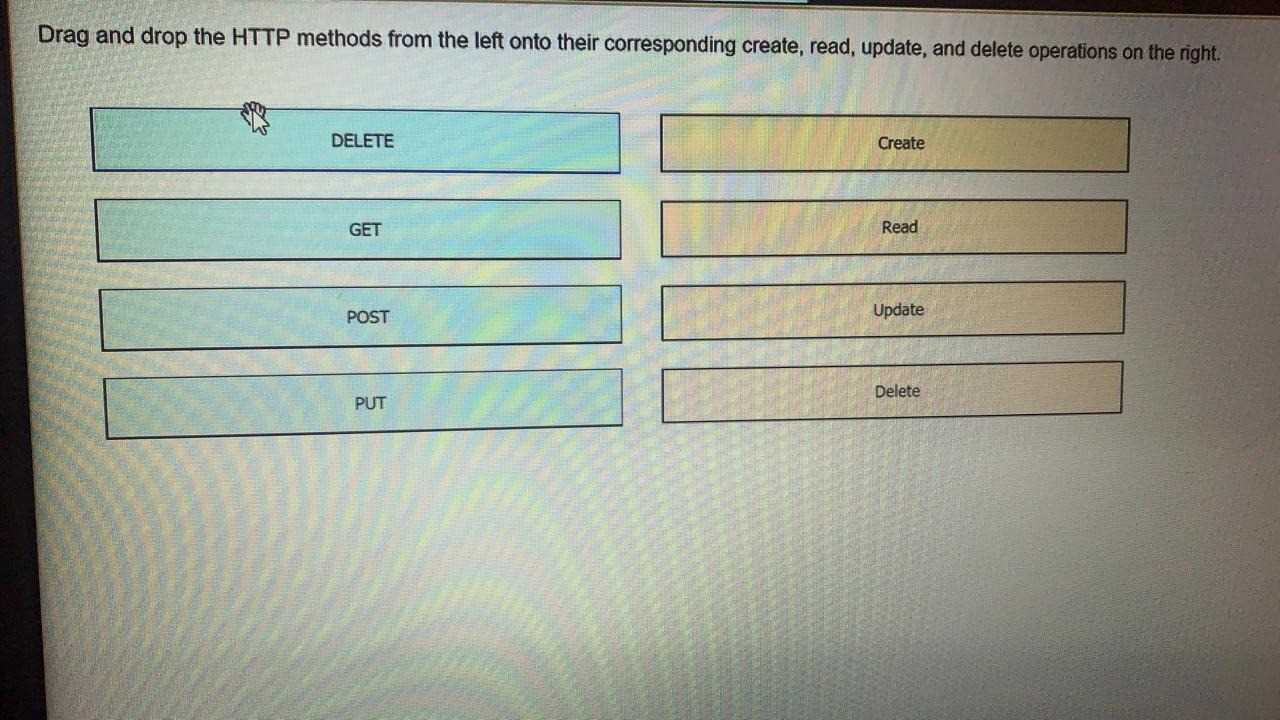
Answer :
Post
Get
Put
Delete
Comments
Question 10
Which two descriptions can be given to an application that is interacting with a webhook? (Choose
two.)
- A. Processor
- B. Codec
- C. Listener
- D. Receiver
- E. Transaction monitor
Answer:
CD
Explanation:
In the context of webhooks, an application that interacts with a webhook can be described as a
Listener or Receiver:
Listener: The application waits for incoming HTTP POST requests sent by the webhook.
Receiver: The application receives the data payloads from the webhook when certain events occur.
Reference:
Cisco DevNet Associate Certification Guide: Chapter on Webhooks and Event-Driven Programming.
Webhook documentation and best practices.
Comments
Page 1 out of 48
Viewing questions 1-10 out of 481
page 2