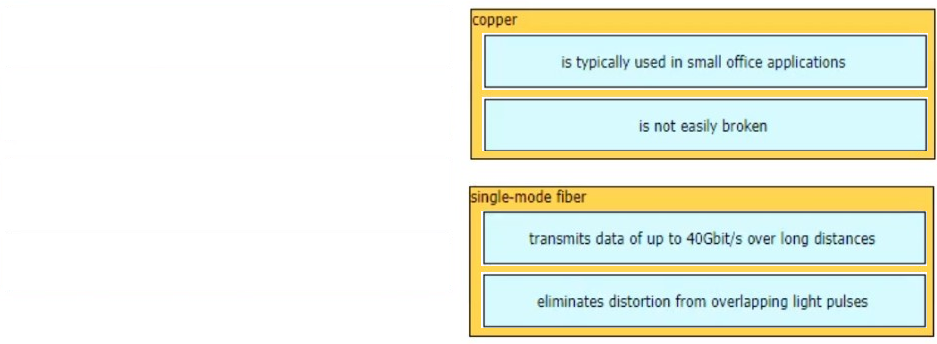
Copper:
- Is typically used in small office applications
- Is not easily broken
Single-mode fiber:
- Eliminates distortion from overlapping light pulses
- Transmits data of up to 40Gbit/s over long distances

Refer to the exhibit. The IPv6 address for the LAN segment on router R2 must be configured using the EUI-64 format. When configured which ipv6 address is produced by the router?
a
What must be considered before deploying virtual machines?
a
SIMULATION
Guidelines
This is a lab item in which tasks will be performed on virtual devices
Refer to the Tasks tab to view the tasks for this lab item.
Refer to the Topology tab to access the device console(s) and perform the tasks.
Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
All necessary preconfigurations have been applied.
Do not change the enable password or hostname for any device.
Save your configurations to NVRAM before moving to the next item.
Click Next at the bottom of the screen to submit this lab and move to the next question.
When Next is clicked the lab closes and cannot be reopened.
Topology

Tasks
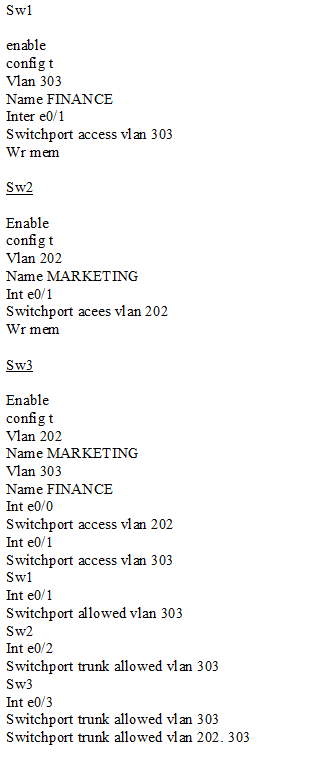
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted across any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 202: MARKETING
VLAN 303: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.


DRAG DROP
Drag and drop the characteristic from the left onto the cable type on the right.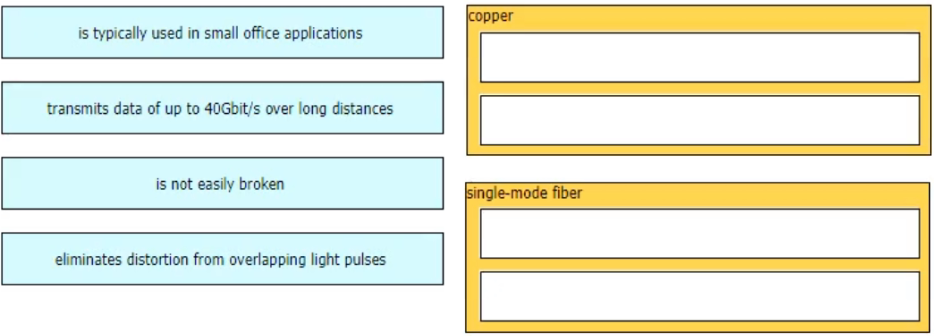
Copper:
- Is typically used in small office applications
- Is not easily broken
Single-mode fiber:
- Eliminates distortion from overlapping light pulses
- Transmits data of up to 40Gbit/s over long distances
a grandes rasgos se puede aceptar lo descrito, sin embargo la fibra tampoco es facil de romper debido a su revestimiento, sea tanto para troncales o para acceso

Refer to the exhibit. Which outcome is expected when PC_A sends data to PC_B after their initial communication?
c
What is the function of the controller in a software-defined network?
c
What is a characteristic of encryption in wireless networks?
d

Refer to the exhibit. Each router must be configured with the last usable IP address in the subnet. Which configuration fulfills this requirement?
d
Which protocol does a REST API use to communicate?
d
Which device separates networks by security domains?
b