Question 1
What is a difference between SOAR and SIEM?
- A. SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
- B. SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
- C. SOAR receives information from a single platform and delivers it to a SIEM
- D. SIEM receives information from a single platform and delivers it to a SOAR
Answer:
A
Comments
Question 2
What is the difference between mandatory access control (MAC) and discretionary access control
(DAC)?
- A. MAC is controlled by the discretion of the owner and DAC is controlled by an administrator
- B. MAC is the strictest of all levels of control and DAC is object-based access
- C. DAC is controlled by the operating system and MAC is controlled by an administrator
- D. DAC is the strictest of all levels of control and MAC is object-based access
Answer:
B
Comments
Question 3
What is the practice of giving employees only those permissions necessary to perform their specific
role within an organization?
- A. least privilege
- B. need to know
- C. integrity validation
- D. due diligence
Answer:
A
Explanation:
The principle of least privilege states that users and processes should be granted only the minimum
permissions necessary to perform their specific role or function within an organization. This reduces
the attack surface and limits the potential damage of a compromised account or process. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 1: Security
Concepts, Lesson 1.2: Security Principles
Cisco Certified CyberOps Associate Overview
, Exam Topics, 1.1 Explain the CIA triad
Comments
Question 4
What is the virtual address space for a Windows process?
- A. physical location of an object in memory
- B. set of pages that reside in the physical memory
- C. system-level memory protection feature built into the operating system
- D. set of virtual memory addresses that can be used
Answer:
D
Explanation:
The virtual address space for a Windows process is the set of virtual memory addresses that can be
used by the process. Each process has its own virtual address space that is isolated from other
processes. The virtual address space is divided into regions that have different attributes, such as
read-only, read-write, execute, and so on. The virtual address space is mapped to the physical
memory by the operating system using a data structure called a page table. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 4: Host-Based
Analysis, Lesson 4.1: Windows Operating System
Virtual Address Space
Comments
Question 5
Which security principle is violated by running all processes as root or administrator?
- A. principle of least privilege
- B. role-based access control
- C. separation of duties
- D. trusted computing base
Answer:
A
Explanation:
Running all processes as root or administrator violates the principle of least privilege, which states
that users and processes should be granted only the minimum permissions necessary to perform
their specific role or function within an organization. Running all processes as root or administrator
gives them full access and control over the system, which increases the risk of unauthorized actions,
malicious attacks, and accidental errors. It also makes it easier for attackers to escalate their
privileges and compromise the system. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 1: Security
Concepts, Lesson 1.2: Security Principles
Cisco Certified CyberOps Associate Overview
, Exam Topics, 1.1 Explain the CIA triad
Comments
Question 6
What is the function of a command and control server?
- A. It enumerates open ports on a network device
- B. It drops secondary payload into malware
- C. It is used to regain control of the network after a compromise
- D. It sends instruction to a compromised system
Answer:
D
Explanation:
A command and control server (C2 or C&C) is a server that is used by attackers to communicate with
and control compromised systems, such as bots, zombies, or backdoors. The C2 server can send
instructions to the compromised systems, such as executing commands, downloading files,
uploading data, or launching attacks. The C2 server can also receive information from the
compromised systems, such as system information, keystrokes, screenshots, or
credentials. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 3: Network
Intrusion Analysis, Lesson 3.4: Malware
Cisco Certified CyberOps Associate Overview
, Exam Topics, 3.4 Compare and contrast types of
malware
Comments
Question 7
What is the difference between deep packet inspection and stateful inspection?
- A. Deep packet inspection is more secure than stateful inspection on Layer 4
- B. Stateful inspection verifies contents at Layer 4 and deep packet inspection verifies connection at Layer 7
- C. Stateful inspection is more secure than deep packet inspection on Layer 7
- D. Deep packet inspection allows visibility on Layer 7 and stateful inspection allows visibility on Layer
Answer:
D
Explanation:
Deep packet inspection (DPI) and stateful inspection are two techniques that are used by firewalls
and other network security devices to inspect and filter network traffic. Stateful inspection allows
visibility on Layer 4 (transport layer) of the OSI model, which means it can track the state of TCP or
UDP connections and filter packets based on source and destination IP addresses, ports, and
protocols. Deep packet inspection allows visibility on Layer 7 (application layer) of the OSI model,
which means it can inspect the contents and payloads of packets and filter packets based on
application-specific criteria, such as signatures, keywords, URLs, or behaviors. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 2: Security
Monitoring, Lesson 2.2: Network Security Monitoring Tools
Cisco Certified CyberOps Associate Overview
, Exam Topics, 2.2 Describe the impact of network
security monitoring tools on data privacy
Comments
Question 8
Which evasion technique is a function of ransomware?
- A. extended sleep calls
- B. encryption
- C. resource exhaustion
- D. encoding
Answer:
B
Explanation:
Encryption is an evasion technique that is a function of ransomware, which is a type of malware that
encrypts the victim’s files or system and demands a ransom for the decryption key. Encryption is
used by ransomware to prevent the victim from accessing their data and to avoid detection by
antivirus or other security tools. Encryption can also be used by other types of malware to hide their
communication, configuration, or payload from analysis. Reference:
Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) v1.0
, Module 3: Network
Intrusion Analysis, Lesson 3.4: Malware
Cisco Certified CyberOps Associate Overview
, Exam Topics, 3.4 Compare and contrast types of
malware
Comments
Question 9
Refer to the exhibit.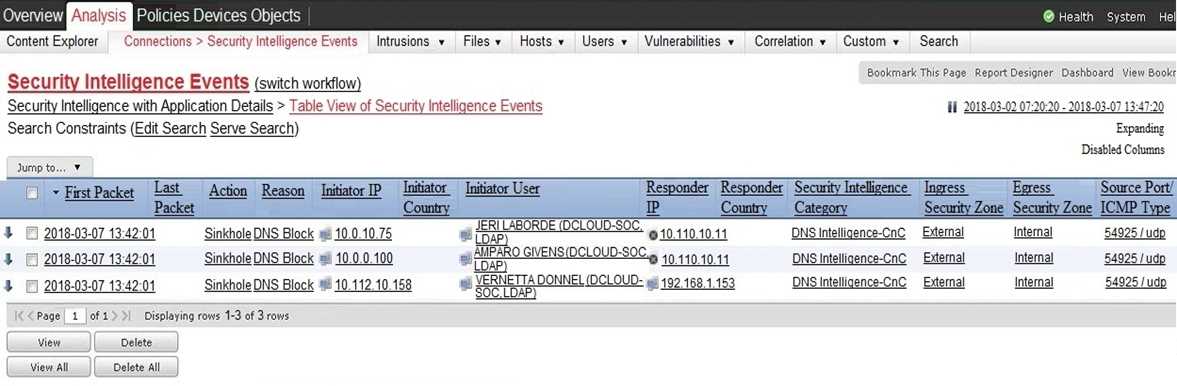
Which two elements in the table are parts of the 5-tuple? (Choose two.)
- A. First Packet
- B. Initiator User
- C. Ingress Security Zone
- D. Source Port
- E. Initiator IP
Answer:
D, E
Explanation:
The 5-tuple refers to the five different values that are used to define a specific communication
session in a network. These values include the source IP address, destination IP address, source port,
destination port, and the protocol in use. In this case, option D (Source Port) and option E (Initiator
IP) are parts of the 5-tuple. Reference :=
Cisco Cybersecurity Operations Fundamentals
Comments
Question 10
DRAG DROP
Drag and drop the security concept on the left onto the example of that concept on the right.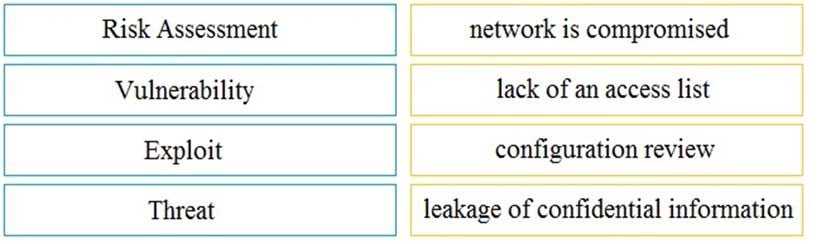
Answer:
None
Explanation:
Comments
Page 1 out of 45
Viewing questions 1-10 out of 451
page 2