Question 1
Which macOS security feature encrypts the entire macOS volume?
- A. FileVault
- B. Gatekeeper
- C. System Integrity Protection (SIP)
- D. XProtect
Answer:
A
Explanation:
The CCST Cybersecurity Study Guide highlights FileVault as the macOS full-disk encryption tool.
"FileVault is macOS’s built-in full-disk encryption feature. It encrypts the contents of the entire
startup disk to help prevent unauthorized access to the information stored on the drive, even if the
device is lost or stolen."
(CCST Cybersecurity, Endpoint Security Concepts, Disk Encryption section, Cisco Networking
Academy)
A is correct: FileVault provides complete volume encryption.
B (Gatekeeper) controls app installation by verifying code signatures.
C (System Integrity Protection) protects system files from modification.
D (XProtect) is macOS’s built-in malware detection system.
Comments
Question 2
You are reviewing your company’s disaster recovery plan.
Which two daily data backup actions should the plan include? (Choose 2.)
- A. Back up the data to removable media and store it off-site.
- B. Back up each department’s data to a separate local server.
- C. Back up the data by using cloud services.
- D. Back up the data by using RAID on a local external hard drive with a secondary power source.
Answer:
AC
Explanation:
The CCST Cybersecurity Study Guide emphasizes that backups should be stored off-site or in the
cloud to ensure recovery even if the primary location is damaged or compromised.
"A comprehensive disaster recovery plan includes performing regular backups and ensuring copies
are stored in locations not subject to the same physical risks as the primary site. Off-site storage and
cloud-based backups provide resilience against local disasters."
(CCST Cybersecurity, Essential Security Principles, Backup and Disaster Recovery section, Cisco
Networking Academy)
A is correct: Off-site removable media ensures recovery even if the main site is destroyed.
B is incorrect: Local-only backups are vulnerable to the same risks as production systems.
C is correct: Cloud services provide geographically separate storage with automated redundancy.
D is incorrect: RAID is for hardware fault tolerance, not a complete backup solution.
Comments
Question 3
Which two passwords follow strong password policy guidelines? (Choose 2.)
- A. Wh@tareyouDo1ngtoday4
- B. Feb121978
- C. Fluffy#
- D. 1mPressm3!
Answer:
AD
Explanation:
The CCST Cybersecurity course defines a strong password as one that:
Is at least 8–12 characters long
Uses a mix of uppercase, lowercase, numbers, and symbols
Avoids dictionary words, personal information, and predictable patterns
"Strong passwords combine length, complexity, and unpredictability, making them resistant to brute
force and dictionary attacks."
(CCST Cybersecurity, Essential Security Principles, Authentication and Access Control section, Cisco
Networking Academy)
A is correct: It’s long, mixed case, includes numbers and symbols, and is not easily guessable.
B is incorrect: It’s based on a date, which is predictable.
C is incorrect: Short and based on a dictionary word.
D is correct: Uses complexity and length with leetspeak for added unpredictability.
Comments
Question 4
Your home network seems to have slowed down considerably. You look at the home router GUI and
notice that an unknown host is attached to the network.
What should you do to prevent this specific host from attaching to the network again?
- A. Create an IP access control list.
- B. Implement MAC address filtering.
- C. Block the host IP address.
- D. Change the network SSID.
Answer:
B
Explanation:
The CCST Cybersecurity course explains that MAC address filtering is a network access control
method that allows only approved device hardware addresses to connect. While not foolproof
against spoofing, it can block a specific device from reconnecting to a small home network.
"MAC address filtering restricts network access to devices whose unique hardware addresses are
explicitly allowed. This can be used to block known unauthorized devices from reconnecting."
(CCST Cybersecurity, Basic Network Security Concepts, Wireless Security Controls section, Cisco
Networking Academy)
A is incorrect: IP ACLs are better for controlling traffic types, not blocking specific devices at the
router level.
B is correct: It prevents the device’s hardware address from reconnecting.
C is temporary since the host can get a new IP via DHCP.
D may hide the network but will not stop a determined attacker who can still detect it.
Comments
Question 5
HOTSPOT
For each statement, select True if it is a common motivation to commit cyber attacks or False if it is
not.
Note: You will receive partial credit for each correct selection.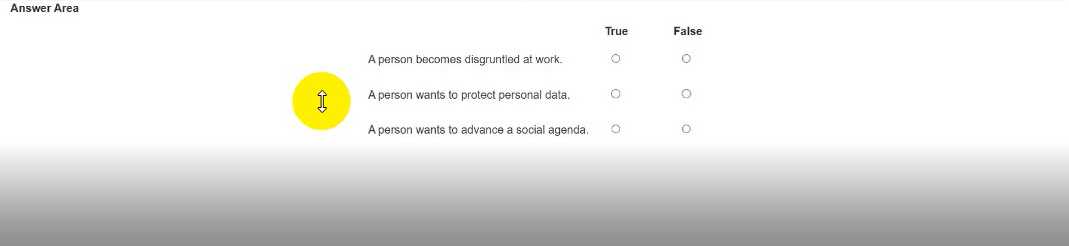
Answer:
None
Explanation: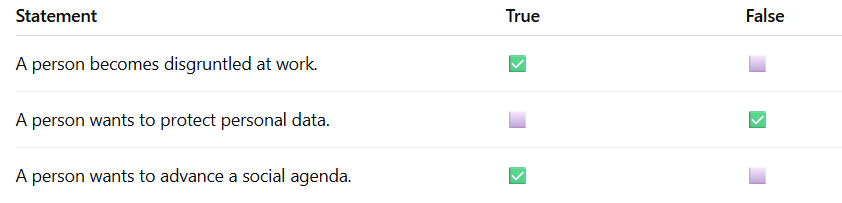
The CCST Cybersecurity Study Guide outlines common motivations for cyberattacks, which include:
Financial gain
Revenge or personal grievance (e.g., disgruntled employees)
Ideological or political purposes (hacktivism)
Espionage and intelligence gathering
"Cyberattack motivations range from financial and competitive advantage to personal vendettas and
advancing political or social causes. Disgruntled insiders may misuse access privileges to harm an
organization, while hacktivists target systems to promote social or political messages."
(CCST Cybersecurity, Essential Security Principles, Threat Actor Motivations section, Cisco
Networking Academy)
Being disgruntled at work → common insider threat motivation (True)
Wanting to protect personal data → defensive action, not a reason to commit an attack (False)
Wanting to advance a social agenda → hacktivist motivation (True)
Comments
Question 6
What should you create to prevent spoofing of the internal network?
- A. A NAT rule
- B. An ACL
- C. A record in the host file
- D. A DNS record
Answer:
B
Explanation:
The CCST Cybersecurity Study Guide states that Access Control Lists (ACLs) can be used to filter traffic
based on IP addresses and block packets that appear to originate from the internal network but
arrive from external interfaces (IP spoofing).
"ACLs can prevent spoofing by dropping traffic from external sources that claim to have an internal
source address. Configuring ACLs on the perimeter firewall or router is a common countermeasure
for IP spoofing."
(CCST Cybersecurity, Basic Network Security Concepts, ACLs and Traffic Filtering section, Cisco
Networking Academy)
A (NAT rule) changes IP addresses but does not inherently prevent spoofing.
B (ACL) is correct because it can enforce anti-spoofing filters.
C (host file) only affects name resolution locally.
D (DNS record) is for domain mapping, not spoofing prevention.
Comments
Question 7
A remote worker is visiting a branch office to attend face-to-face meetings. The worker tries to
associate their company laptop with the branch wireless access point (WAP) but is unable to do so.
What is a possible cause?
- A. The SSID is not broadcasting.
- B. The WAP is configured for MAC address filtering.
- C. The IP address of the laptop is not correct.
- D. The WAP is using open authentication.
Answer:
B
Explanation:
The CCST Cybersecurity material explains that MAC address filtering is a wireless security measure
that allows only devices with approved hardware addresses to connect. If the laptop’s MAC address
is not on the allow list, the connection will be blocked even if the SSID is correct.
"Wireless access points can be configured with MAC address filters to limit network access to
authorized devices. If a device's MAC address is not on the permitted list, the connection will fail
regardless of credentials."
(CCST Cybersecurity, Basic Network Security Concepts, Wireless Security section, Cisco Networking
Academy)
A is unlikely because non-broadcast SSIDs can still be manually connected to.
B is correct: MAC address filtering would block an unregistered device.
C would cause IP issues after association, not prevent initial connection.
D (open authentication) would allow connection, so it’s not the cause here.
Comments
Question 8
Which security assessment of IT systems verifies that PII data is available, accurate, confidential, and
accessible only by authorized users?
- A. Risk framing
- B. Cyber Kill Chain
- C. Workflow management
- D. Information assurance
Answer:
D
Explanation:
The CCST Cybersecurity study material defines Information Assurance (IA) as the practice of
managing information-related risks to ensure data availability, integrity, confidentiality,
authentication, and non-repudiation. It specifically applies to sensitive information like PII
(Personally Identifiable Information).
"Information assurance involves the protection and validation of data so that it remains accurate,
confidential, and available only to authorized users. IA ensures the trustworthiness of information,
particularly when handling sensitive or regulated data such as PII."
(CCST Cybersecurity, Vulnerability Assessment and Risk Management, Information Assurance
section, Cisco Networking Academy)
A (Risk framing) is part of risk management planning but does not verify data integrity and
confidentiality directly.
B (Cyber Kill Chain) is an attack lifecycle model.
C (Workflow management) is about process efficiency, not data protection.
D is correct: Information Assurance addresses the availability, accuracy, and confidentiality of
sensitive data.
Comments
Question 9
DRAG DROP
Move each definition from the list on the left to the correct CIA Triad term on the right.
Note: You will receive partial credit for each correct answer.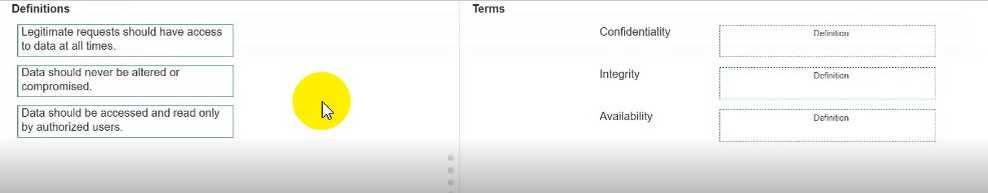
Answer:
None
Explanation: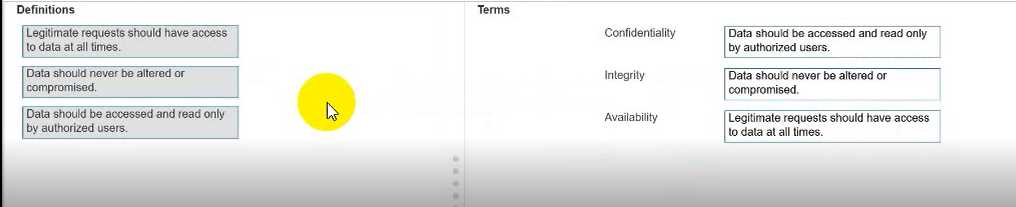
The CCST Cybersecurity Study Guide describes the CIA Triad as the foundational model for
information security:
Confidentiality
"Confidentiality ensures that sensitive information is accessed only by authorized individuals and is
protected from unauthorized disclosure."
Integrity
"Integrity ensures that data remains accurate, complete, and unaltered except by authorized
processes or users."
Availability
"Availability ensures that information and systems are accessible to authorized users when needed."
(CCST Cybersecurity, Essential Security Principles, CIA Triad section, Cisco Networking Academy)
Comments
Question 10
What is the primary purpose of running a vulnerability scan on your network?
- A. To identify and document the locations of customer and financial databases
- B. To automatically prioritize security weaknesses for immediate remediation
- C. To determine whether systems are subject to CVEs that could be exploited by adversaries
- D. To correlate event logs on multiple servers in order to generate intrusion alerts
Answer:
C
Explanation:
The CCST Cybersecurity Study Guide states that vulnerability scanning is an automated process used
to identify known security weaknesses in systems, software, and network devices. These scans
compare system configurations and software versions against databases of known vulnerabilities,
such as the Common Vulnerabilities and Exposures (CVE) list.
"A vulnerability scan is an automated test that checks systems and networks for known weaknesses
by matching them against a database of vulnerabilities such as CVEs. This allows administrators to
identify exploitable conditions before they are leveraged by attackers."
(CCST Cybersecurity, Vulnerability Assessment and Risk Management, Vulnerability Scanning section,
Cisco Networking Academy)
A is asset discovery, not vulnerability scanning.
B may be part of remediation planning but is not the primary purpose.
C is correct: Scans detect if systems have vulnerabilities associated with CVEs.
D describes SIEM (Security Information and Event Management) log correlation, not vulnerability
scanning.
Comments
Page 1 out of 4
Viewing questions 1-10 out of 50
page 2