Question 1
View the rule below. What does the pen-symbol in the left column mean?
- A. Those rules have been published in the current session.
- B. Rules have been edited by the logged in administrator, but the policy has not been published yet.
- C. Another user has currently locked the rules for editing.
- D. The configuration lock is present. Click the pen symbol in order to gain the lock.
Answer:
B
Comments
Question 2
What object type would you use to grant network access to an LDAP user group?
- A. Access Role
- B. User Group
- C. SmartDirectory Group
- D. Group Template
Answer:
B
Comments
Question 3
Which of the following technologies extracts detailed information from packets and stores
that information in state tables?
- A. INSPECT Engine
- B. Next-Generation Firewall
- C. Packet Filtering
- D. Application Layer Firewall
Answer:
B
Comments
Question 4
An administrator is creating an IPsec site-to-site VPN between his corporate office and
branch office. Both offices are protected by Check Point Security Gateway managed by the
same Security Management Server (SMS). While configuring the VPN community to specify
the pre-shared secret, the administrator did not find a box to input the pre-shared secret. Why
does it not allow him to specify the pre-shared secret?
- A. The Gateway is an SMB device
- B. The checkbox “Use only Shared Secret for all external members” is not checked
- C. Certificate based Authentication is the only authentication method available between two Security Gateway managed by the same SMS
- D. Pre-shared secret is already configured in Global Properties
Answer:
C
Comments
Question 5
Which of the following is NOT a policy type available for each policy package?
- A. Threat Emulation
- B. Access Control
- C. Desktop Security
- D. Threat Prevention
Answer:
A
Comments
Question 6
Which SmartConsole tab is used to monitor network and security performance?
- A. Manage & Settings
- B. Security Policies
- C. Gateway & Servers
- D. Logs & Monitor
Answer:
D
Comments
Question 7
Which option in a firewall rule would only match and allow traffic to VPN gateways for one
Community in common?
- A. All Connections (Clear or Encrypted)
- B. Accept all encrypted traffic
- C. Specific VPN Communities
- D. All Site-to-Site VPN Communities
Answer:
C
Comments
Question 8
____________ is the Gaia command that turns the server off.
- A. sysdown
- B. exit
- C. halt
- D. shut-down
Answer:
C
Comments
Question 9
Which software blade enables Access Control policies to accept, drop, or limit web site
access based on user, group, and/or machine?
- A. Application Control
- B. Data Awareness
- C. Identity Awareness
- D. Threat Emulation
Answer:
A
Comments
Question 10
What is a role of Publishing?
- A. The Publish operation sends the modifications made via SmartConsole in the private session and makes them public
- B. The Security Management Server installs the updated policy and the entire database on Security Gateways
- C. The Security Management Server installs the updated session and the entire Rule Base on Security Gateways
- D. Modifies network objects, such as servers, users, services, or IPS profiles, but not the Rule Base
Answer:
A
Comments
Question 11
You are the Check Point administrator for Alpha Corp. You received a call that one of the
users is unable to browse the Internet on their new tablet which is connected to the company
wireless, which goes through a Check Point Gateway. How would you review the logs to see
what is blocking this traffic?
- A. Open SmartLog and connect remotely to the wireless controller
- B. Open SmartEvent to see why they are being blocked
- C. Open SmartDashboard and review the logs tab
- D. Open SmartLog and filter for the IP address of the tablet
Answer:
D
Comments
Question 12
Examine the sample Rule Base.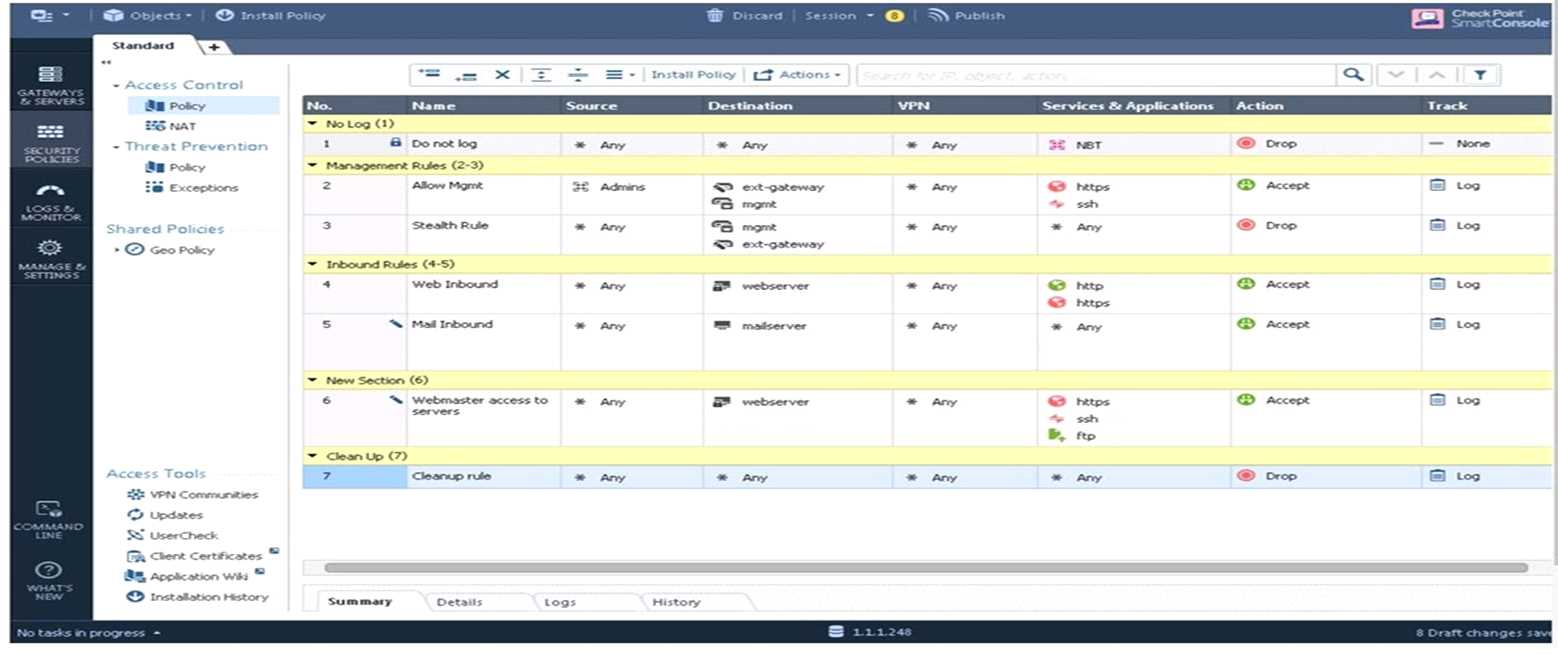
What will be the result of a verification of the policy from SmartConsole?
- A. No errors or Warnings
- B. Verification Error. Empty Source-List in Rule 5 (Mail Inbound)
- C. Verification Error. Rule 4 (Web Inbound) hides Rule 6 (Webmaster access)
- D. Verification Error. Rule 7 (Clean-Up Rule) hides Implicit Clean-up Rule
Answer:
C
Comments
Question 13
Each cluster, at a minimum, should have at least ___________ interfaces.
- A. Five
- B. Two
- C. Three
- D. Four
Answer:
C
Comments
Question 14
Which key is created during Phase 2 of a site-to-site VPN?
- A. Pre-shared secret
- B. Diffie-Hellman Public Key
- C. Symmetrical IPSec key
- D. Diffie-Hellman Private Key
Answer:
C
Comments
Question 15
Which tool is used to enable cluster membership on a Gateway?
- A. SmartUpdate
- B. cpconfig
- C. SmartConsole
- D. sysconfig
Answer:
B
Comments
Page 1 out of 35
Viewing questions 1-15 out of 522
page 2