Question 1
Quantum computers threaten traditional cryptography because they provide polynomial solutions to
mathematically "hard" problems
- A. True
- B. False
Answer:
A
Comments
Question 2
Transactions can be added to DAG-based distributed ledgers without being validated but the same is
not true for blockchain.
- A. True
- B. False
Answer:
A
Comments
Question 3
Which smart contract auditing strategy determines the inputs that will cause different parts of the
code to run?
- A. Symbolic Execution
- B. Taint Analysis
- C. Dynamic Code Analysis
- D. Control Flow Analysis
Answer:
A
Comments
Question 4
Which of the following is designed to allow someone to prove they know a secret without revealing
it?
- A. Confidential Transaction
- B. Ring Signature
- C. Zero-Knowledge Proof
- D. Stealth Address
Answer:
C
Comments
Question 5
In which of the following attacks targeting Proof of Stake does an attacker create a divergent chain
and race to make their chain longer than the real chain?
- A. Selfish Mining Attack
- B. Long-Range Attack
- C. Double-Spend Attack
- D. 51% Attack
Answer:
B
Comments
Question 6
Which type of attack misuses Internet protocols to attack the blockchain? Select all that apply.
- A. Denial of Service
- B. Eclipse
- C. Sybil
- D. Routing
Answer:
ABC
Comments
Question 7
Which of the following are common inputs to the algorithm to select the next block creator in Proof
of Stake? Select all that apply
- A. Age of User Account
- B. Time Since Last Chosen to Create a Block
- C. Stake Size
- D. User Activity on the Blockchain
Answer:
B, C, D
Comments
Question 8
Which algorithm was adopted by Bitcoin's creator for use as a consensus mechanism?
- A. Proof of Stake
- B. Proof of Space
- C. Proof of Work
- D. Proof of Activity
Answer:
C
Comments
Question 9
Which of the following blockchains has a built-in consensus algorithm?
- A. Ethereum
- B. Corda
- C. Hyperledger
Answer:
A
Comments
Question 10
This sample code is vulnerable to which of the following attacks?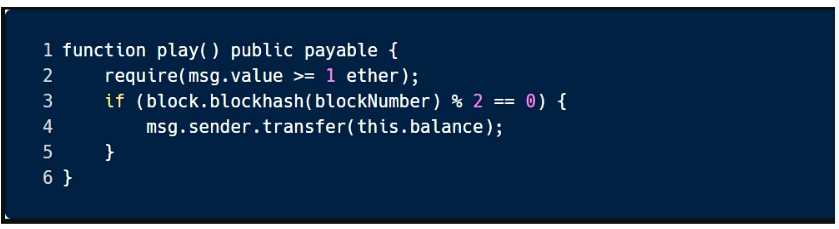
- A. Bad Randomness
- B. Reentrancy
- C. Arithmetic
- D. Unchecked Return Values
Answer:
A
Comments
Page 1 out of 9
Viewing questions 1-10 out of 91
page 2