Question 1
The key difference between encryption and hashing is that encrypted strings can be reversed back
into their original decrypted form if you have the right key?
- A. TRUE
- B. FALSE
Answer:
A
Comments
Question 2
What is a logic gate in electronics and computer science?
- A. A logic gate usually takes in 2 inputs and gives out 1 output. The inputs and outputs are binary values, meaning they can be both 1 and 0.
- B. A logic gate usually takes in 3 inputs and gives out 2 output. The inputs and outputs are binary values, meaning they can be 1 or 0.
- C. A logic gate usually takes in 2 inputs and gives out 6 output. The inputs and outputs are binary values, meaning they can be both 1 and 0.
- D. A logic gate usually takes in 2 inputs and gives out 1 output. The inputs and outputs are binary values, meaning they can be 1 or 0.
Answer:
D
Explanation:
A logic gate usually takes in 2 inputs and gives out 1 output. The inputs and outputs are binary
values, meaning they can be 1 or 0. A XOR logic gate takes in 2 binary inputs and gives out a high
output ONLY when the inputs are different. Meaning, if A and B are inputted to a XOR gate then the
out C will be 1 ONLY when A is not equal to B.
Comments
Question 3
Ethereum is considered to be a ______________type of blockchain.
- A. Permissionless
- B. Permission Based
- C. Hybrid
- D. Private
Answer:
A
Explanation:
Permissionless - anyone can join Anyone can run a node, run mining software/hardware, access a
wallet and write data onto and transact within the blockchain (as long as they follow the rules of the
bitcoin blockchain). There is no way to censor anyone, ever, on the permissionless bitcoin blockchain.
Comments
Question 4
Your company working for is now considering the blockchain. They would like to perform a POC with
R3 Cord
a. The CIO was reading about different blockchain consensus algos and would like to understand
what type of consensus algos is used with Corda.
What is the best answer?
- A. R3 Corda is a pluggable blockchain and allows the enterprise flexibility
- B. R3 Corda is a byzantine fault tolerant blokchain
- C. R3 Corda is a proof of stake based blockchain
- D. R3 Corda is a proof of work based blockchain
Answer:
A
Explanation:
Corda does not share the same requirements as Bitcoin: we require absolute certainty over
transaction finality and we need to know who our counterparts are. So we had the freedom – and
took this opportunity – to solve the consensus problem in a different way. In particular, Corda solves
the privacy issue in a number of manners, primarily by allowing for separation of consensus into a
service which we call the Notary Cluster. Corda was designed for business from the start. It has no
cryptocurrency built into the platform and does not require mining-style consensus, which imposes
great cost with little business benefit.
Comments
Question 5
Secure Hash Algorithm (SHA-256) output is always 256 bits or 32 bytes in length regardless of the
length of the input (even if input is millions of bytes). Select best answer.
- A. NSA is spying on us so what’s it matters.
- B. Depends on input
- C. False
- D. True
Answer:
D
Explanation:
SHA stands for Secure Hash Algorithm. This is used to prove data integrity. The same input(s) will
always produce the exact same output. This output is always 256 bits or 32 bytes in length regardless
of the length of the input (even if input is millions of bytes).
Comments
Question 6
In the Ethereum EVM there are two types of memory areas. (Select two.)
- A. Storage
- B. Database
- C. Memory
- D. Persistent
- E. Ephemeral
Answer:
A,C
Comments
Question 7
What are some advantages of Proof of Stake(POS) mining over Proof of Work(POW) mining? (Select
three.)
- A. Energy efficient in regards to that it could consume for electricity as compared to PoW
- B. Faster Hashing algorithms
- C. No need for expensive compared to POW
- D. Faster validations compared to POW
- E. Better blockchain security compared to POW
Answer:
A,C,D
Explanation:
This eliminates the below challenges from PoW and believed to have an advantage.
No need of expensive hardware (a normal laptop or computer running the respective coin’s Validator
client will do as long as your laptop or computer is online)
Energy efficient as it won’t consume high electricity as PoW does More loyal Validators As higher the
stake the Validators have for a long time, more chances for the Validator to be picked up for “forging”
and earn the transaction fee Faster validations
Comments
Question 8
Application Specific Integrated Circuit (ASIC) are used always in enterprise blockchains.
- A. TRUE
- B. FALSE
Answer:
B
Explanation:
ASICS are generally used in blockchains such as BTC that have a Proof of Work consensus due to
competition
Comments
Question 9
What type of encryption is shown below and is commonly used in blockchain cryptography?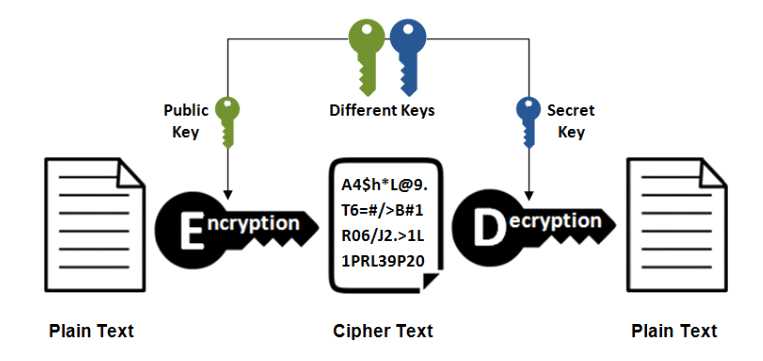
- A. Diffie-Hellman
- B. Asymmetric Encryption
- C. Synchronous
- D. Asynchronous
- E. Symmetric Encryption
Answer:
B
Explanation:
Asymmetric cryptography utilizes two different keys, a public key and a private to encrypt and
decrypt a particular data. The use of one key cancels out the use of the other.
Comments
Question 10
An encryption algorithm transforms plain text into cipher text using a key?
- A. TRUE
- B. FALSE
Answer:
A
Comments
Page 1 out of 22
Viewing questions 1-10 out of 229
page 2