amazon AWS Certified SysOps Administrator (SOA-C01) practice test
Last exam update: Jun 25 ,2025
Question 1
A user is measuring the CPU utilization of a private data center machine every minute. The machine provides the aggregate
of data every hour, such as Sum of data, Min value, Max value, and Number of Data points.
The user wants to send these values to CloudWatch. How can the user achieve this?
- A. Send the data using the put-metric-data command with the aggregate-values parameter
- B. Send the data using the put-metric-data command with the average-values parameter
- C. Send the data using the put-metric-data command with the statistic-values parameter
- D. Send the data using the put-metric-data command with the aggregate –data parameter
Answer:
C
Explanation:
AWS CloudWatch supports the custom metrics. The user can always capture the custom data and upload the data to
CloudWatch using CLI or APIs. The user can publish the data to CloudWatch as single data points or as an aggregated set
of data points called a statistic set using the command put-metric-data. When sending the aggregate data, the user needs to
send it with the parameter statistic-values: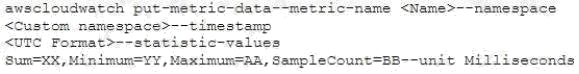
Question 2
A SysOps Administrator has an AWS CloudFormation template of the companys existing infrastructure in us-west-2. The
Administrator attempts to use the template to launch a new stack in eu-west-1, but the stack only partially deploys, receives
an error message, and then rolls back.
Why would this template fail to deploy? (Choose two.)
- A. The template referenced an IAM user that is not available in eu-west-1
- B. The template referenced an Amazon Machine Image (AMI) that is not available in eu-west-1
- C. The template did not have the proper level of permissions to deploy the resources
- D. The template requested services that do not exist in eu-west-1
- E. CloudFormation templates can be used only to update existing services
Answer:
B C
Question 3
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the
CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months.
What is the process to rotate the key?
- A. Enable automatic key rotation for the CMK, and specify a period of 6 months.
- B. Create a new CMK with new imported material, and update the key alias to point to the new CMK.
- C. Delete the current key material, and import new material into the existing CMK.
- D. Import a copy of the existing key material into a new CMK as a backup, and set the rotation schedule for 6 months.
Answer:
A
Explanation:
Cryptographic best practices discourage extensive reuse of encryption keys. To create new cryptographic material for your
AWS Key Management Service (AWS KMS) customer master keys (CMKs), you can create new CMKs, and then change
your applications or aliases to use the new CMKs. Or, you can enable automatic key rotation for an existing CMK.
When you enable automatic key rotation for a customer managed CMK, AWS KMS generates new cryptographic material for
the CMK every year. AWS KMS also saves the CMK's older cryptographic material in perpetuity so it can be used to decrypt
data that it encrypted. AWS KMS does not delete any rotated key material until you delete the CMK. Reference:
https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html
Question 4
An enterprise is using federated Security Assertion Markup Language (SAML) to access the AWS Management Console.
How should the SAML assertion mapping be configured?
- A. Map the group attribute to an AWS group. The AWS group is assigned IAM policies that govern access to AWS resources.
- B. Map the policy attribute to IAM policies the federated user is assigned to. These policies govern access to AWS resources.
- C. Map the role attribute to an AWS role. The AWS role is assigned IAM policies that govern access to AWS resources.
- D. Map the user attribute to an AWS user. The AWS user is assigned specific IAM policies that govern access to AWS resources.
Answer:
C
Explanation:
Reference: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_create_saml_assertions.html
Question 5
A database is running on an Amazon RDS Multi-AZ DB instance. A recent security audit found the database to be out of
compliance because it was not encrypted.
Which approach will resolve the encryption requirement?
- A. Log in to the RDS console and select the encryption box to encrypt the database.
- B. Create a new encrypted Amazon EBS volume and attach it to the instance.
- C. Encrypt the standby replica in the secondary Availability Zone and promote it to the primary instance.
- D. Take a snapshot of the RDS instance, copy and encrypt the snapshot, and then restore to the new RDS instance.
Answer:
A
Question 6
A companys use of AWS Cloud services is quickly growing, so a SysOps Administrator has been asked to generate details
of daily spending to share with management.
Which method should the Administrator choose to produce this data?
- A. Share the monthly AWS bill with management.
- B. Use AWS CloudTrail Logs to access daily costs in JSON format.
- C. Set up a daily Cost and Usage Report and download the output from Amazon S3.
- D. Monitor AWS costs with Amazon CloudWatch and create billing alerts and notifications.
Answer:
C
Question 7
Which of the following statements is true of tags and resource identifiers for EC2 instances?
- A. You can't select instances by their tags for stoppage, termination, or deletion
- B. You don't need to specify the resource identifier while terminating a resource.
- C. You don't need to specify the resource identifier while stopping a resource.
- D. You can select instances by their tags for stoppage, termination, or deletion
Answer:
A
Explanation:
You can assign tags only to resources that already exist. You can't terminate, stop, or delete a re-source based solely on its
tags; you must specify the resource identifier. For example, to delete snap-shots that you tagged with a tag key called
DeleteMe, you must use the DeleteSnapshots action with the resource identifiers of the snapshots, such as snap-
1234567890abcdef0. To identify re-sources by their tags, you can use the DescribeTags action to list all of your tags and
their associated resources.
Reference: http://docs.amazonwebservices.com/AWSEC2/latest/UserGuide/Using_Tags.html
Question 8
What should a SysOps Administrator do to ensure a company has visibility into maintenance events performed by AWS?
- A. Run a script that queries AWS Systems Manager for upcoming maintenance events, and then push these events to an Amazon SNS topic to which the Operations team is subscribed.
- B. Query the AWS Health API for upcoming maintenance events and integrate the results with the companys existing operations dashboard.
- C. Integrate the AWS Service Health Dashboard’s RSS feed into the company’s existing operations dashboard.
- D. Use Amazon Inspector to send notifications of upcoming maintenance events to the Operations team distribution list.
Answer:
C
Explanation:
Reference: https://aws.amazon.com/premiumsupport/technology/personal-health-dashboard/
Question 9
A user has created a VPC with public and private subnets using the VPC Wizard. The VPC has CIDR 20.0.0.0/16. The
private subnet uses CIDR 20.0.0.0/24. Which of the below mentioned entries are required in the main route table to allow the
instances in VPC to communicate with each other?
- A. Destination : 20.0.0.0/24 and Target : VPC
- B. Destination : 20.0.0.0/16 and Target : ALL
- C. Destination : 20.0.0.0/0 and Target : ALL
- D. Destination : 20.0.0.0/24 and Target : Local
Answer:
D
Explanation:
Option A doesn't use standard AWS terminology (you don't route to "VPC"), and because the mask is /24, it would only allow
the instances in the private subnet to communicate with each other, not all the instances in the VPC as the question asked.
Here's an example VPC route table for a public subnet (i.e. it routes to the IGW). Option D is the correct one.
Question 10
You have set up an IAM policy for your users to access Elastic Load Balancers and you know that an IAM policy is a JSON
document that consists of one or more statements. Which of the following elements is not a part of the statement in an IAM
policy document?
- A. Action
- B. Resource
- C. Effect
- D. Key
Answer:
D
Explanation:
When you attach a policy to a user or group of users to control access to your load balancer, it al-lows or denies the users
permission to perform the specified tasks on the specified resources.
An IAM policy is a JSON document that consists of one or more statements. Each statement is structured as follows:
Effect: The effect can be Allow or Deny. By default, IAM users don't have permission to use re-sources and API actions, so
all requests are denied. An explicit allow overrides the default. An ex-plicit deny overrides any allows.
Action: The action is the specific API action for which you are granting or denying permission.
Resource: The resource that's affected by the action. With many Elastic Load Balancing API ac-tions, you can restrict the
permissions granted or denied to a specific load balancer by specifying its Amazon Resource Name (ARN) in this statement.
Otherwise, you can use the * wildcard to specify all of your load balancers. Condition: You can optionally use conditions to
control when your policies in effect.
Reference: http://docs.aws.amazon.com/ElasticLoadBalancing/latest/DeveloperGuide/UsingIAM.html
Question 11
Network ACLs in a VPC operate at the ______.
- A. TCP level
- B. instance level
- C. subnet level
- D. gateway level
Answer:
C
Explanation:
Security Groups in VPC operate at the instance level, providing a way to control the incoming and outgoing instance traffic.
In contrast, network ACLs operate at the subnet level, providing a way to control the traffic that flows through the subnets of
your VPC.
Reference: http://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Security.html
Question 12
A user is launching an instance with EC2. Which options below should the user consider before launching an instance?
- A. Select the region where the instance is being launched.
- B. All choices are correct.
- C. Select the instance type.
- D. Select the OS of the AMI.
Answer:
B
Explanation:
Regarding Amazon EC2, when launching an instance, the user needs to select the region the in-stance would be launched
from. While launching, the user needs to plan for the instance type and the OS of the instance. Reference:
http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-launch-instance_linux.html
Question 13
An instance has enabled basic monitoring only for CloudWatch. What is the minimum time period available for basic
monitoring?
- A. 60 seconds
- B. 360 seconds
- C. 300 seconds
- D. 240 seconds
Answer:
C
Explanation:
When a user is setting up an alarm on the EC2 instance metric, the time period should be equal to or more than the metric
frequency. For basic monitoring, the metric is monitored at every 5 minutes (300 seconds). Reference:
http://docs.aws.amazon.com/AmazonCloudWatch/latest/APIReference/API_MetricDatum.html
Question 14
A SysOps Administrator runs a web application that is using a microservices approach whereby different responsibilities of
the application have been divided in a separate microservice running on a different Amazon EC2 instance. The Administrator
has been tasked with reconfiguring the infrastructure to support this approach.
How can the Administrator accomplish this with the LEAST administrative overhead?
- A. Use Amazon CloudFront to log the URL and forward the request.
- B. Use Amazon CloudFront to rewrite the header based on the microservice and forward the request.
- C. Use an Application Load Balancer (ALB) and do path-based routing.
- D. Use a Network Load Balancer (NLB) and do path-based routing.
Answer:
C
Explanation:
Reference: https://docs.aws.amazon.com/elasticloadbalancing/latest/application/tutorial-load-balancer-routing.html
Question 15
A companys Marketing department generates gigabytes of assets each day and stores them locally. They would like to
protect the files by backing them up to AWS. All the assets should be stored on the cloud, but the most recent assets should
be available locally for low latency access.
Which AWS service meets the requirements?
- A. Amazon EBS
- B. Amazon EFS
- C. Amazon S3
- D. AWS Storage Gateway
Answer:
D
Explanation:
Reference: https://aws.amazon.com/storagegateway/faqs/